Container security with Trivy
Trivy is a simple and comprehensive vulnerability/misconfiguration/secret scanner for containers and other artifacts. Trivy detects vulnerabilities of OS packages (Alpine, RHEL, CentOS, etc.) and language-specific packages (Bundler, Composer, npm, yarn, etc.). In addition, Trivy scans Infrastructure as Code (IaC) files such as Terraform and Kubernetes, to detect potential configuration issues that expose your deployments to the risk of attack. Trivy also scans hardcoded secrets like passwords, API keys and tokens. Trivy is easy to use. Just install the binary and you're ready to scan. All you need to do for scanning is to specify a target such as an image name of the container.
When we are preparing a container, many parts are involved, including:
- Project source code
- Installation of system packages
- Installation of project dependencies (using NPM, Composer, etc.)
For the first part, obviously programmers do all the work to ensure the project has no security issues. But what about the next two parts? For example, you need the OpenSSL package and you install it at the beginning of your Dockerfile using apt. Now, if this version of OpenSSL installed has a security bug, what happens? You put it in your container and deploy it somewhere.
Let's go further... You develop a Laravel project and install its requirements using Composer. One of these requirements, like guzzle, may have a specific bug, similar to the previous case.
If a team wants to review each package and find vulnerabilities in them and set versions accordingly, they should hire another team... How many times should they do this? If a new version is released every week, should they spend several hours every week manually checking everything? Surely, we should not forget security issues in the meantime. This is where Trivy comes in!
What is Trivy?
This project has been around for almost a year and has now reached version v0.52.0. The Trivy's job is to scan your containers or system files to make sure there are no security issues. It is specifically designed for use in CI tools to automate the process I described earlier. It has some good features such as:
- Identifying security issues in various parts
- Simple
- Fast
- Easy to install and use
- High accuracy
- Suitable for CI
- Support for various platforms

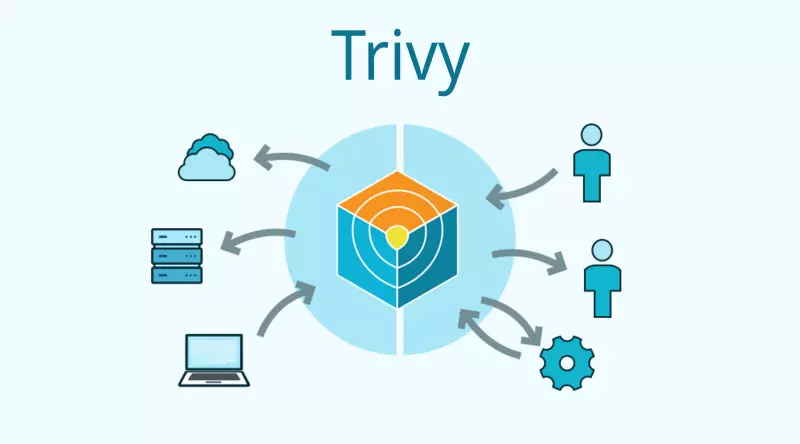
Trivy is a comprehensive and versatile security scanner. Trivy has scanners that look for security issues, and targets where it can find those issues.
Targets (what Trivy can scan):
- Container Image
- Filesystem
- Git Repository (remote)
- Virtual Machine Image
- Kubernetes
- AWS
Scanners (what Trivy can find there):
- OS packages and software dependencies in use (SBOM)
- Known vulnerabilities (CVEs)
- IaC issues and misconfigurations
- Sensitive information and secrets
- Software licenses